-
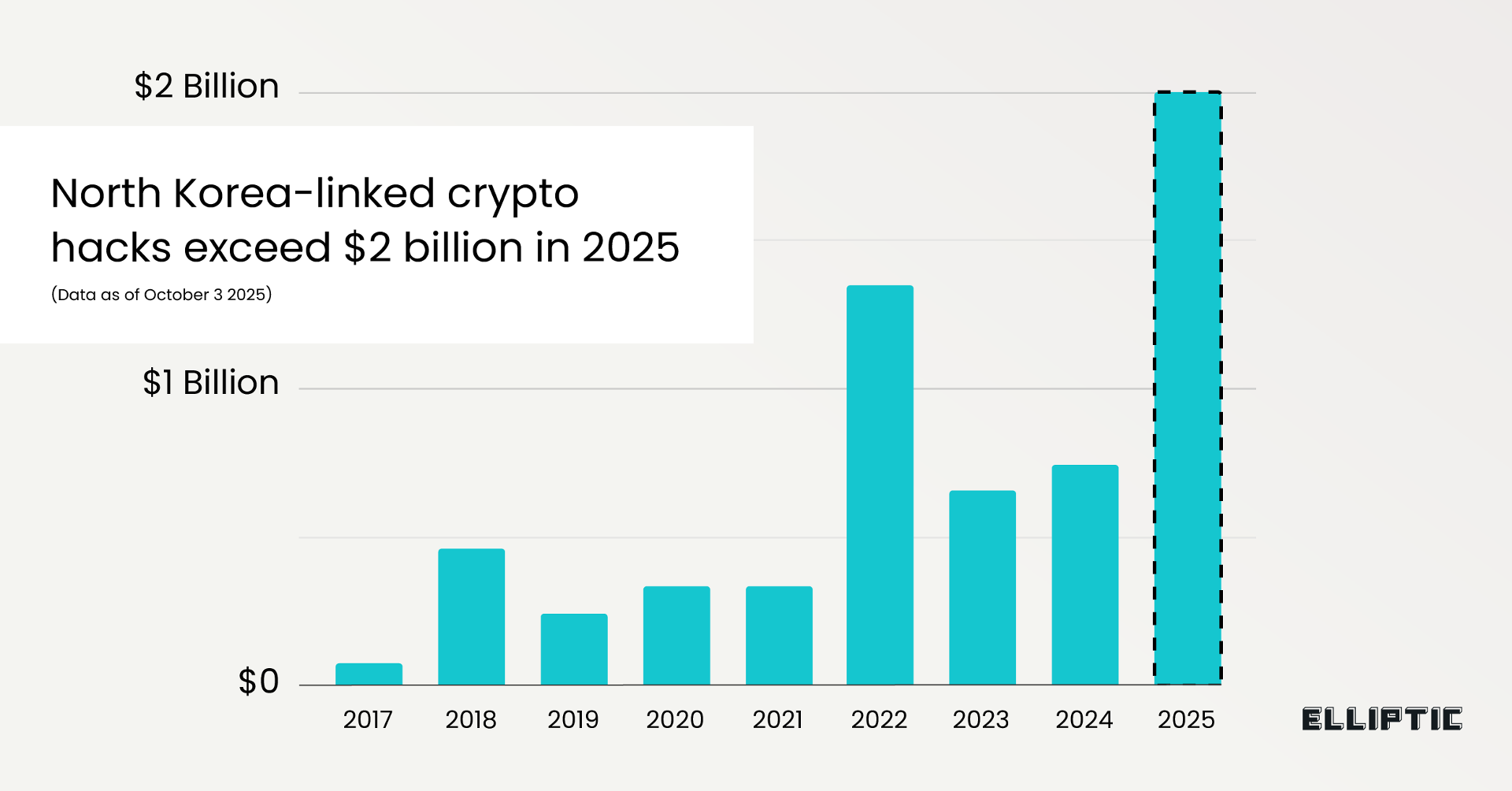
<Elliptic> North Korea's crypto hackers have stolen over $2 billion in 2025Analysis (2025)
<TRM> 2025-12-18, North Korea and the Industrialization of Cryptocurrency Theft
<US Department of Treasury> 2025-7-24, Treasury Sanctions Clandestine IT Worker Network Funding the DPRK’s Weapons Programs.
<Chainalysis> 2025-10-1, DPRK IT Workers: Inside North Korea’s Crypto Laundering Network
<US Justice Department> 2025-1-23, Two North Korean Nationals and Three Facilitators Indicted for Multi-Year Fraudulent Remote Information Technology Worker Scheme that Generated Revenue for the Democratic People’s Republic of Korea (IT Worker)
<US Justice Department> 2024-12-12, Fourteen North Korean Nationals Indicted for Carrying Out Multi-Year Fraudulent Information Technology Worker Scheme and Related Extortions (IT Worker)
<UK, Office of Financial Sanctions Implementation> 2024-9-12, Advisory on North Korean IT Workers.
<38 North> 2024-8-21, North Korea’s International Network for Artificial Intelligence Research.
<US Justice Department> 2024-8-8, Justice Department Disrupts North Korean Remote IT Worker Fraud Schemes Through Charges and Arrest of Nashville Facilitator (IT Worker)
<KnowBe4 (cyber security company)> 2024-06-23, How a North Korean Fake IT Worker Tried to Infiltrate Us.
-
<U.S. Departments of State and Treasury, and the Federal Bureau of Investigation> 2022-5-16, GUIDANCE ON THE DEMOCRATIC PEOPLE’S REPUBLIC OF KOREA INFORMATION TECHNOLOGY WORKERS.
-
<UN Security Council Arri-formula> 2025-1-14, Security Council Arria-formula on "Commercial Spyware and the Maintenance of International Peace and Security".
DPRK Cyber Actor and IT worker ties to UN Designated Entities
(Source: MSMT)
Nearly all DPRK cyber units and overseas IT workers identified in this report operate under or in support of UN-designated DPRK entities, including the Reconnaissance General Bureau, Ministry of National Defense, Ministry of Atomic Energy Industry, and the Munitions Industry Department, as well as the Korean Workers’ Party, which is subject to an assets freeze.
DPRK cyber actors and IT workers deployed abroad typically function through front companies that publicly represent these state entities. These front companies facilitate sanctions-violating activities—such as IT services, procurement, and money laundering—on behalf of UN-designated DPRK entities, activities that UN Member States are obligated to prevent.
Organization and Units Overview
Park Jin Hyok
RGB Cyber Actor
Source: FBI.
Park Jin Hyok is a US-indicted, state-sponsored North Korean programmer linked to the Reconnaissance General Bureau, accused of orchestrating large-scale cyber intrusions and theft of fiat and virtual currency as part of the Lazarus Group/APT38 network.
Arrest warrants and charges
June 8, 2018: U.S. federal arrest warrant issued for conspiracy to commit wire fraud and computer intrusion.
December 8, 2020: Superseding arrest warrant issued by the U.S. District Court (Central District of California), charging conspiracy to commit wire fraud, bank fraud, and computer fraud.
<Elliptic> DPRK Surpasses $2 Billion in Crypto Theft in 2025, Led by the $1.46B Bybit Hack and Advanced Laundering Tactics
January 6, 2026 (*The article was published by Elliptic on October 7, 2025)
<Summary>
Elliptic reports that DPRK-linked hackers have already stolen over $2 billion in cryptocurrency in 2025.
This figure includes more than thirty additional hacks attributed to the DPRK, notably incorporating the February 2025 $1.46 billion theft from Bybit, demonstrating a sustained operational tempo rather than isolated incidents despite increased global awareness and defensive measures.
A growing share of victims now includes high-net-worth individuals, reflecting a strategic pivot toward personally targeted theft rather than exclusively exploiting exchanges or on-chain protocols.
The campaign shows a clear rise in social engineering attacks, marking a shift from earlier attacks where technical flaws in smart contracts or infrastructure were the primary attack vectors.
Post-theft laundering strategies have become increasingly sophisticated and layered, involving repeated mixing, cross-chain transfers, obscure blockchains, and the exploitation of “refund addresses” to redirect assets to fresh wallets, reducing traceability and investigative visibility.
December 31, 2025 (*The article was published by Chainalysis on October 1, 2025)
<Chainalysis>From Fake IT Jobs to Fiat Cash: Mapping the DPRK IT Worker Crypto Laundering Network
DPRK IT workers generate cryptocurrency revenue by infiltrating global IT jobs, often being paid in stablecoins that are attractive to OTC traders as an off-ramp to fiat, with funds ultimately financing North Korea’s weapons programs.
Sanctions and enforcement actions target key facilitators, including the OFAC-designated Sim Hyon Sop (a Korea Kwangson Banking Corp rep who received tens of millions in DPRK IT worker crypto) and Lu Huaying, a Chinese OTC trader based in the UAE sanctioned for laundering DPRK IT worker proceeds.
DPRK IT workers are deployed via front companies such as Chinyong Information Technology Cooperation Company, sanctioned by OFAC and the Republic of Korea for employing DPRK IT labor overseas, and they use obfuscation techniques (VPNs, fake IDs) to conceal their identities.
After receiving stablecoin payments, DPRK IT worker funds are laundered through methods like chain-hopping, token swaps, and mixing, then consolidated and moved through intermediaries—including accounts tied to Kim Sang Man, a DPRK national and representative of Chinyong Information Technology Cooperation Company, Sim Hyon Sop, and OTC facilitator Lu Huaying—before conversion to fiat.
Read the full report in Japanese (北朝鮮IT労働者による暗号資産マネーロンダリングネットワークの内幕)
Who is Sim Hyon Sop?
Sim Hyon-Sop has allegedly played a central role in North Korea’s counterfeit cigarette trade since at least 2009, using front companies, false shipping records, and bulk cash payments to evade US sanctions.
Between 2021 and 2023, he and co-conspirators imported tobacco into the DPRK and laundered US dollar payments, with proceeds benefiting the regime’s WMD programs.
Us authorities charged Sim with conspiracy to violate the IEEPA, bank fraud, and money laundering, issuing an arrest warrant in 2023 and indictments in 2025.
On July 24, 2025, the U.S. State Department is offering up to $7 million for information leading to his arrest or conviction; notably, on April 26, 2023, it had already announced a reward of up to $5 million for information related to his alleged sanctions evasion involving illicit tobacco trade and money laundering.
Source:
US DOJ Civil Forfeiture Complaint
April 26, 2023: Reward of up to USD 5 million
US State Dept offers rewards for info leading to arrests of 3 transnational criminals
FBI Wanted Poster (archived) SIM HYON-SOP - FBI
July 24, 2025: Reward increased to up to USD 7 million
December 18, 2025
<TRM> DPRK and the Industrialization of Crypto Theft: How a Single State Actor Dominated Global Hack Losses in 2025
Cryptocurrency theft has become industrialized
The DPRK has systematized crypto theft into a repeatable and organized operation, combining cyber units, overseas IT workers, and laundering intermediaries rather than relying on isolated hacks.North Korea linked to the majority of global crypto hack losses in 2025
In 2025, more than USD 2.7 billion was stolen in cryptocurrency hacks worldwide, and well over half of that total was linked to a single nation-state actor: North Korea, according to TRM Labs.Fewer incidents, larger returns
DPRK-linked operations increasingly focus on high-value compromises, allowing outsized returns from a smaller number of attacks rather than frequent low-impact exploits.Human and organizational access is central
TRM Labs highlights the DPRK’s reliance on people-and-platform compromise, including embedded IT workers, impersonation, and abuse of internal trust at crypto-related firms.“Chinese Laundromat” as the off-chain exit mechanism
Stolen funds ultimately move into a Chinese-language laundering ecosystem, where intermediaries coordinate via WeChat and conduct off-chain settlement into Chinese yuan (CNY) or goods, marking the point at which assets leave the blockchain.
Source: DPRK Monitor.
December 18, 2025
<Chainalysis>2025 Crypto Theft Trends: DPRK Sets New Records With Fewer Attacks
North Korean hackers stole $2.02 billion in cryptocurrency in 2025, a 51% year-over-year increase, pushing their all-time total to $6.75 billion despite fewer attacks.
The DPRK is achieving larger thefts with fewer incidents, often by embedding IT workers inside crypto services or using sophisticated impersonation tactics targeting executives.
The DPRK shows clear preferences for Chinese-language money laundering services, bridge services, and mixing protocols, with a 45-day laundering cycle following major thefts.
Individual wallet compromises surged to 158,000 incidents affecting 80,000 unique victims in 2025, though total value stolen ($713M) decreased from 2024.
Despite increased Total Value Locked in DeFi, hack losses remained suppressed in 2024-2025, suggesting improved security practices are making a meaningful difference.
Read the full report in Japanese (北朝鮮による暗号資産窃取、年間で過去最高の20億ドルに)
August 8, 2025
Old Game, New Name: Sobaeksu and DPRK’s WMD Legacy
The US government has recently designated the Korea Sobaeksu Trading Company (Sobaeksu) for asset freezing, citing its involvement in foreign currency-generating activities conducted by DPRK IT workers.
However, by examining past DPRK Panel reports, it becomes clear that Sobaeksu is in fact connected to companies previously involved in WMD development—namely, NAMCHONGANG TRADING CORPORATION (NCG) and KOREA MINING DEVELOPMENT TRADING CORPORATION (KOMID).
Sobaeksu
朝鲜小白水联合会社
Namchonggang
KOMID
Yun Ho-Jin
Source: DPRK NM Inventory Safeguards Agreement - 4 May 1992 by IAEA Imagebank by Flicker (Edited by DPRK Monitor).NCG was previously engaged in North Korea’s nuclear development, particularly in procurement related to uranium enrichment, while KOMID was involved in missile transactions. These DPRK entities linked to the development and sale of WMDs have continued their operations under different names.
UNSCR 2270 (2016) pointed out that NCG had changed its name to Namhung Trading Corporation (Namhung).
A review of corporate information registered in China shows that Namhung and the Beijing office of Sobaeksu shared the same address.
The representative of Sobaeksu’s Beijing office is Yun Ho-Jin, who was formerly the head of NCG. Yun Ho-Jin (윤호진 in Korean, 尹浩真 in Chinese) is listed under UN sanctions and is a former DPRK diplomat who was involved in uranium enrichment-related procurement at least as far back as the 1990s. His name is currently registered as the representative of Sobaeksu’s Beijing office.
Kim Chol Nam (김철남 in Korean, 金哲南 in Chinese), listed as a director of Sobaeksu’s Dandong office, is also registered as the representative of Korea Changgwang Trading Corporation in Beijing. Past Panel investigations have confirmed that Korea Changgwang Trading Corp is an alias for KOMID.
August 3, 2025
Part of DPRK’s Hard Currency Network
While the US has imposed sanctions on DPRK’s activities in Southeast Asia, the UN Security Council DPRK Panel of Experts (POE) report—covering the newly sanctioned individuals Kim Se Un and Sobaeksu—offers key new information. DPRK Monitor shares additional context below.
DPRK individuals operate or control multiple registered entities in various countries and engage in several distinct areas—including IT, trading, finance, and, in some cases, money laundering, military logistics, or procurement. These individuals often obtain passports from host countries or assume foreign identities to travel across multiple jurisdictions—thereby enhancing both their mobility and concealment.
Kim Se Un
김 세 운
Date of Birth: 25 March 1978
Passport: Passport 390120007 (DPRK) issued 09 Jan 2020 expires 09 Jan 2025 (individual)
Source: US Department of State.According to the US State Department, Kim Se Un is a North Korean representative of Korean Sobaeksu Trading Company (Sobaeksu) and was involved in a scheme from April 2021 to June 2023 to smuggle tobacco into DPRK and pay in US dollars, violating US sanctions. The operation used false shipping records and bulk cash to evade restrictions.
From Vietnam to Cambodia — A Wider Web
In the past, Kim Se Un also registered company in Cambodia. According to the POE report (S/2023/171, paras.155-157), Kim was the director of the Cambodia-based company U.J Import Export Co., Ltd (struck off by Cambodian authorities in December 2019, Figure 1).
Cooperated with Ri Chol Nam
Moreover, the POE reported Kim cooperated with Ri Chol Nam (리철남) (Figure 2,3), who was involved in money laundering, brokering sales of weapons, diamonds, and gold, and other illicit financial activities linked to the DPRK. Ri also engaged in potential sales of military-related equipment, including bulletproof vests acquired from third countries for resale.
The Expanding DPRK Network: Who’s Next?
DPRK Monitor will update Kim Se Un’s network!
Figure 1
Source: Cambodian corporate registry (Edited by DPRK Monitor).Figure 2
Source: DPRK Monitor.Figure 3
Source: DPRK POE S/2023/171, annex 85.Source: Maltego Graph Visualization (annotated by DPRK Monitor).Use of AI by DPRK
DPRK IT workers may use AI-generated fake ID during job interviews. A report by cyber security company also indicate their use of real-time deepfake technology. The most effective detection method is passing a hand over the face, which disrupts facial landmark tracking. Other recommended techniques include:
Rapid head movements
Exaggerated facial expressions
Sudden lighting changes
Companies are advised to adopt layered detection strategies in coordination with their information security teams. Below is an example of DPRK tactics.
Source: KnowBe4. “The picture (right) is an AI-enhanced version of the person who we interviewed during the hiring process, where the applicant’s face was added over a completely different unrelated person’s “stock photography” picture (left) so they looked more professional with glasses and wearing formal work attire.”
Source: KnowBe4, “North Korean Fake Employees Are Everywhere! How to Protect Your Organization” (Annotated by DPRK Monitor)